Research & Opinion
Don’t Let Your Business Become A Victim Of Cybercrime

A cybersecurity professional enhancing information security of enterprises by identifying risks and threats and helping to implement strategies to prevent those threats from damaging the enterprise’s assets.
“It takes 20 years to build a reputation and few minutes of cyber-incident to ruin it”. Taking your business online can have its benefits, but it can also increase the risk of scams and security threats. Thinking about all the new and varied cyber threats your company faces today can quickly feel overwhelming. Where should you begin, and how can you make sure you’re staying informed?
Here are the four most common types of cyber threats your company may face.
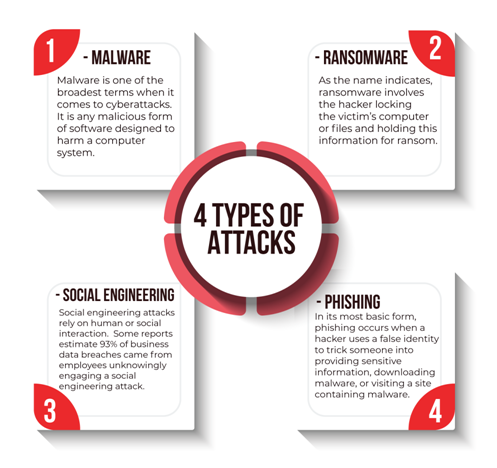
Taking a proactive approach to cyber security will enable you to avoid damaging and disruptive cyber attacks. Cyber security solutions provide digital protection to your business that will ensure your employees aren’t at risk from potential threats such as Adware and Ransomware.
You can’t block blended attacks by blocking every channel, attackers might use without sealing off your business from the outside world. And solutions that monitor and block malware on single channels are only partially effective. It is recommended to implement “multi-layer” security.
What do we mean when we refer to “multi-layer” security?
Multi-layered security refers to a security system that uses numerous components to shield multiple levels or operational layers. The term can also refer to “defensive in depth”, which is based on slightly different ideas, many of which are used to mitigate threats, delay or prevent threats. Following are the cybersecurity strategies to protect your business, customers, and your data from growing cybersecurity threats.
1. Train employees in security principles.
For employees to be able to spot and prevent security breaches, they’ll need a basic education in different ways that cybersecurity threats can present themselves. For the most part, this includes spam, phishing, malware and ransomware, and social engineering.
Explain that passwords are the first line of protection to keep sensitive information safe and hackers at bay. Then, show employees how to set strong passwords that incorporate a combination of letters, numbers, and symbols.
2. Avoid using out of date software and services.
Outdated software doesn’t have patches if vulnerabilities are found, and it can fall prey to far more advanced cyber-attacks. This poses a cacophony of security risks, both due to human malice and the chances of system failure. Having the latest security software, web browser, and operating system are the best defences against viruses, malware, and other online threats.
3. Provide firewall as a defence mechanism.
A firewall is a system that provides network security by filtering incoming and outgoing network traffic based on a set of user-defined rules. In general, the purpose of a firewall is to reduce or eliminate the occurrence of unwanted network communications while allowing all legitimate communication to flow freely. Make sure the operating system’s firewall is enabled or install free firewall software available online. If employees work from home, ensure that their home system(s) are protected by a firewall.
4. Make backup copies of important business data and information.
Regularly backup the data on all systems to avoid loss of data during a security incident. Critical data includes word processing documents, electronic spreadsheets, databases, financial files, human resources files, and accounts receivable/payable files. Backup data automatically if possible, or at least weekly and store the copies either offsite or in the cloud.
5. Control unauthorized access to your assets and limit employee access to data and information.
Prevent access or use of business computers by unauthorized individuals. Laptops can be particularly easy targets for theft or can be lost, so lock them up when unattended. Make sure a separate user account is created for each employee and require strong passwords. Administrative privileges should only be given to trusted IT staff and key personnel. Do not provide any one employee with access to all data systems. Employees should only be given access to the specific data systems that they need for their jobs, and should not be able to install any software without permission.
6. Secure your Wi-Fi networks.
If you have a Wi-Fi network for your workplace, make sure it is secure, encrypted, and hidden. To hide your Wi-Fi network, set up your wireless access point or router, so it does not broadcast the network name, known as Service Set Identifier (SSID). Password protect access to the router.
7. Employ best practices on payment cards.
Work with banks or processors to ensure the most trusted and validated tools and anti-fraud services are being used. You may also have additional security obligations pursuant to agreements with your bank or processor. Isolate payment systems from other less secure programs and don’t use the same computer to process payments and surf the Internet.
8. Use of string passwords and multi-factor authentication.
Require employees to use unique passwords and change passwords every three months. Consider implementing multi-factor authentication that requires additional information beyond a password to gain entry. Check with your vendors that handle sensitive data, especially financial institutions, to see if they offer multi-factor authentication for your account.
Technical fixes and developing a cyber risk culture are good company defences on the front end. The greater the defence upfront, the more benefits companies will see on the back end. You’re more likely to be able to enter new business ventures with clients that will have a greater level of comfort and safety in knowing that you’re educated enough in the discipline of cybersecurity to invest in the proper technical security, products, solutions, and vendors.
Companies that value security help to build strong customer trust.

Shreyal Jain – -Cyber Security Analyst at CyberSmithSECURE














