Cyber Crime
This Is How Hackers Stole Over Rs 2 Cr From 10 ATMs In Kolkata

New Delhi: Law enforcement agencies have requested banks to enhance the alarm system at unprotected ATM kiosks. Instructions came in wake of a sophisticated cyber attack on ATMs in Kolkata. Between May 14 – 22, hackers intercepted the two-way encrypted communications and data system that connects an ATM to a bank’s main server and stole about Rs 2 crore from at least 10 unsecured automated teller machines (ATM) in the city.
The420.in spoke to experts at Noida based Armantec Systems who conducted their analysis on how the attacks of the ATM of Kolkata are being conducted. Here is their detailed finding:
Nature of Attack : The attacks were crafty, where the machines were not physically damaged (and that’s why no triggers were generated and no alarms.). ATM didn’t send any alarms, no physical intrusion.
Nature of attacks on ATM: Let’s understand the standard attacking techniques used by hackers to bypass these logical and communication mechanisms and “cash-out”. As the scope of this document is only to identify the attack types with a minor physical distortion of the machine, we will isolate our analysis with “Logical ATM Attack” vectors only.
The first one in this type is MiTM (Man in the middle) based attacks. This one is the most common, vastly used, and most probably used for the attack on Kolkata’s ATMs. The man-in middle attacks focus on the communication between the host and the ATM PC. This attack can fake the host response for the transactions without debiting the money from the account. An attacker can execute this attack by either implanting malware in the network/machine itself or doing it externally.
“After analyzing the attack pattern on Kolkata’s ATMs, we assume that the hackers are using a BlackBox device. In this attack, a device (usually containing a Raspberry Pi Zero W computer) will connect between the ATM’s PC and the dispenser. This allows the attacker to send cash dispensing commands directly to the ATM without any bank-side validation,” said a senior official of Armantec Systems.

This type of attack can be challenging because internal access to the machine is required, which again requires opening the system’s front panel and exposing the USB connector where this device needs to be connected. This is Old School Method currently on its way out.
“However, we have identified a simpler way which is available, costing only $25 (Rs.1875), and the worst part is it’s available openly, so there is no need to visit DARK-WEB to procure this. This device is a GL.iNet and is attached externally to the ATM but provides the same result (not out of the box, requires custom codes and minor reprogramming, which we will not share here),” explained the official.
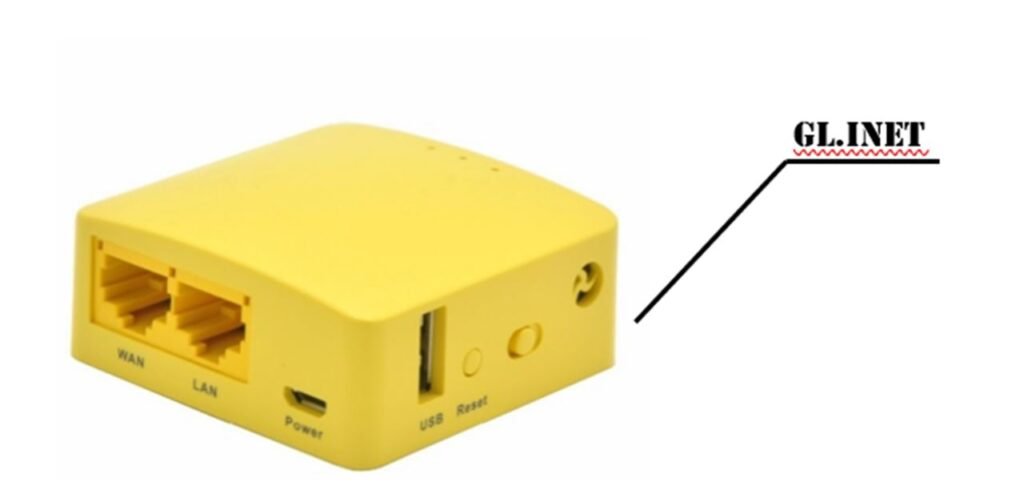
This device works by creating a fake data packet interceptor, processor, and resender (a BlackBox).
Business Logic : In simpler terms, the functionality is executed. The ATMs ask for a communication acknowledgment from the bank, asking whether the card is valid, the requested amount in his account, etc. These BlackBoxes intercept those questions, even before they went to the back, manipulates them, and send them back to the machine’s impersonation that the answers came directly from the back. When an ATM receives these replies, they dispense the requested amount of money without further checking.
However, police investigating Kolkata ATM hack case have hinted it to be the ‘Man-in-the-Middle’ attack, in which fraudsters are suspected to have disconnected ATMs from the bank servers by setting up proxy servers, before withdrawing the money. The targeted ATMs belong to a private bank. The software in the machines was not upgraded, investigating officers said.














