Research & Opinion
One Million Credit Cards Data Up For Sale On Dark Web

Data leakage remains one of the biggest threats for all the major business enterprises, corporate houses and companies.
Losing sensitive data and information can result in massive reputational harm and economic losses. During the last few years, many big data breach incidents have cost corporations millions.
In this digital era, where the volume of data is increasing by the day the threat of its breach and leak has also grown exponentially. Protecting data has become one of the top priorities for companies.
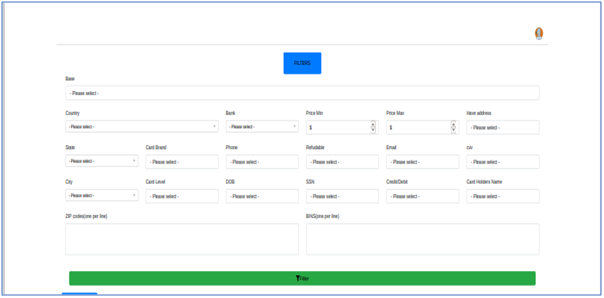
Cyber criminals have now posted details of over one million stolen credit cards, in a bid to promote a new cyber criminal carding marketplace on the dark web. The information on the dark net consists of credit card numbers, expiry dates, CVV numbers, names, addresses, zip codes, email addresses, and phone details of the owners.
Analysis of leaked data shows that it was done through a compromised server of a payment agency. During analysis, it was found that a massive number of cards details from over 100 banks from more than 100 countries have been put on sale on cyber crime forums and dark web.
How To Stay Safe:
Monitor all network access: More monitoring of corporate network traffic can result in higher chances of identifying suspicious activity. It empowers organizations to identify and strengthen security to prevent the possibility of reconnaissance. Also, security policies may need to be revised to protect highly sensitive data.
Identify all sensitive data: Companies need to identify all of the sensitive data that needs to be secured. This data then needs to be correctly classified in line with strict security policies and with all sensitive data identified and correctly classified, it needs to be tailored by the most efficient data leak prevention defences for each data category.
Encrypt all data : Threat actors may find it difficult to exploit data leaks if the data is encrypted.
Secure all endpoints : An endpoint is a remote access point that establishes a connection with a network, either via end-users or autonomously. Firewalls and VPNs offers a base layer of endpoint security but they’re not enough, insider threat actors are often tricked into introducing malware into an ecosystem to bypass these security defenses.
Evaluate all permissions : As an initial response all the permissions should be evaluated to ensure access isn’t being granted to authorized parties. After it is verified all critical data should be categorized to different pools of data.

Writer: Mrityunjay Mishra, a Dark Web Researcher














